Security Awareness Journey — Learning from Chris Kennedy's Targeted Scammer Experience
A deep dive into the sophisticated social engineering attack that targeted security expert Chris Kennedy, and the critical lessons we can all learn about modern scammer tactics, MFA protection, and organizational security awareness.
Security Awareness Journey — Learning from Chris Kennedy’s Targeted Scammer Experience
Dedicated to Chris Kennedy for sharing his incredible security awareness video and helping the community learn from real-world social engineering attacks.
Watch Chris Kennedy’s Original Video: https://lnkd.in/gW6w7W9J
Introduction
In an era where cybersecurity threats are increasingly sophisticated, even security professionals can find themselves targeted by well-orchestrated scammer operations. Chris Kennedy recently shared a powerful security awareness video documenting his firsthand experience with a multi-layered social engineering attack that attempted to compromise his personal accounts.
This blog post breaks down Kennedy’s experience, analyzing the attack timeline, threat sophistication, and the critical security awareness moments that prevented a successful breach.
Watch the full video here: Chris Kennedy’s Security Awareness Journey

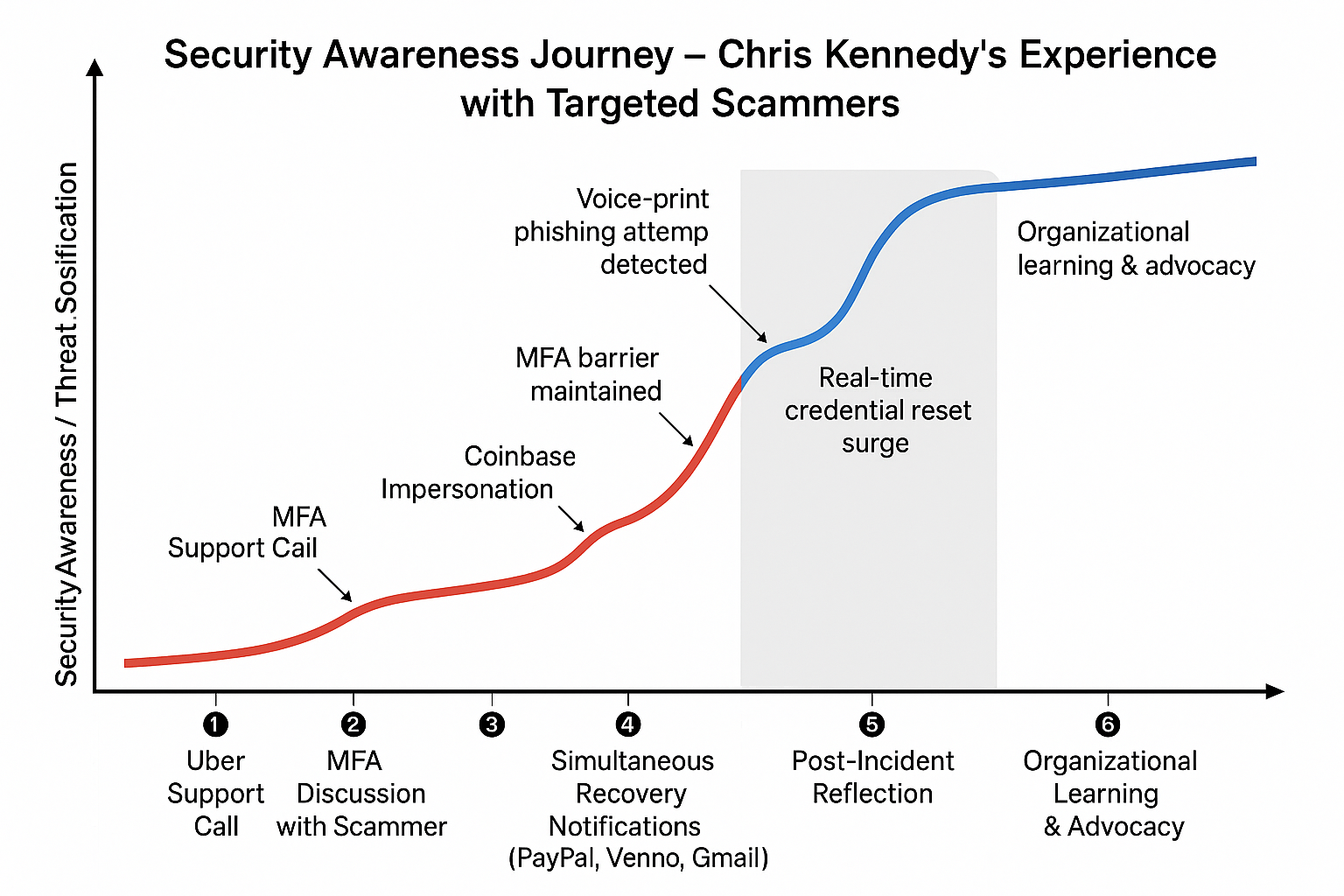
Figure 1: Security Awareness vs. Threat Sophistication Over Time
The Attack Timeline: A Six-Phase Journey
T1: The Uber Support Call — Social Engineering Begins
Timeline: Initial Contact Threat Sophistication: ⚠️ Medium Security Understanding: 🧠 Baseline
The attack began with what appeared to be a legitimate Uber support call. The caller had enough context to seem authentic — order details, account information, and professional demeanor. This is the hallmark of modern social engineering: realistic impersonation.
Key Takeaway: Start of exposure to social engineering; realistic impersonation triggers curiosity rather than immediate suspicion.
Red Flags to Watch For:
- Unsolicited calls claiming to be from known services
- Requests for account verification
- Pressure to act quickly
- Callers who have partial information about your account
T2: MFA Discussion — The First Detection Signal
Timeline: Mid-Call Conversation Threat Sophistication: 🧩 High Security Understanding: 🧩 Elevated
As the conversation progressed, the attacker began discussing Multi-Factor Authentication (MFA) in ways that contradicted how MFA actually works. Kennedy’s security expertise kicked in — he applied security reasoning mid-call and realized something was wrong.
Key Takeaway: Realized attacker’s method contradicts MFA logic; first sign of detection.
Critical MFA Facts:
- Legitimate support NEVER asks you to disable MFA
- Real support teams don’t need your MFA codes
- If someone asks you to approve an MFA prompt they sent, it’s a scam
- MFA is YOUR defense — never share it with anyone
T3: Coinbase Impersonation — Pattern Recognition
Timeline: Follow-up Contact Threat Sophistication: 🚨 Very High Security Understanding: 🧠 Expert
The attack escalated with what appeared to be a Coinbase security alert. But Kennedy recognized this as a layered attack — the scammers were using multiple personas to create a sense of urgency and legitimacy.
Key Takeaway: Identified layered attack and simultaneous credential reset attempts.
Layered Attack Characteristics:
- Multiple “organizations” contacting you about the “same” issue
- Coordinated timing to create panic
- Each contact reinforcing the others’ legitimacy
- Escalating urgency and consequences
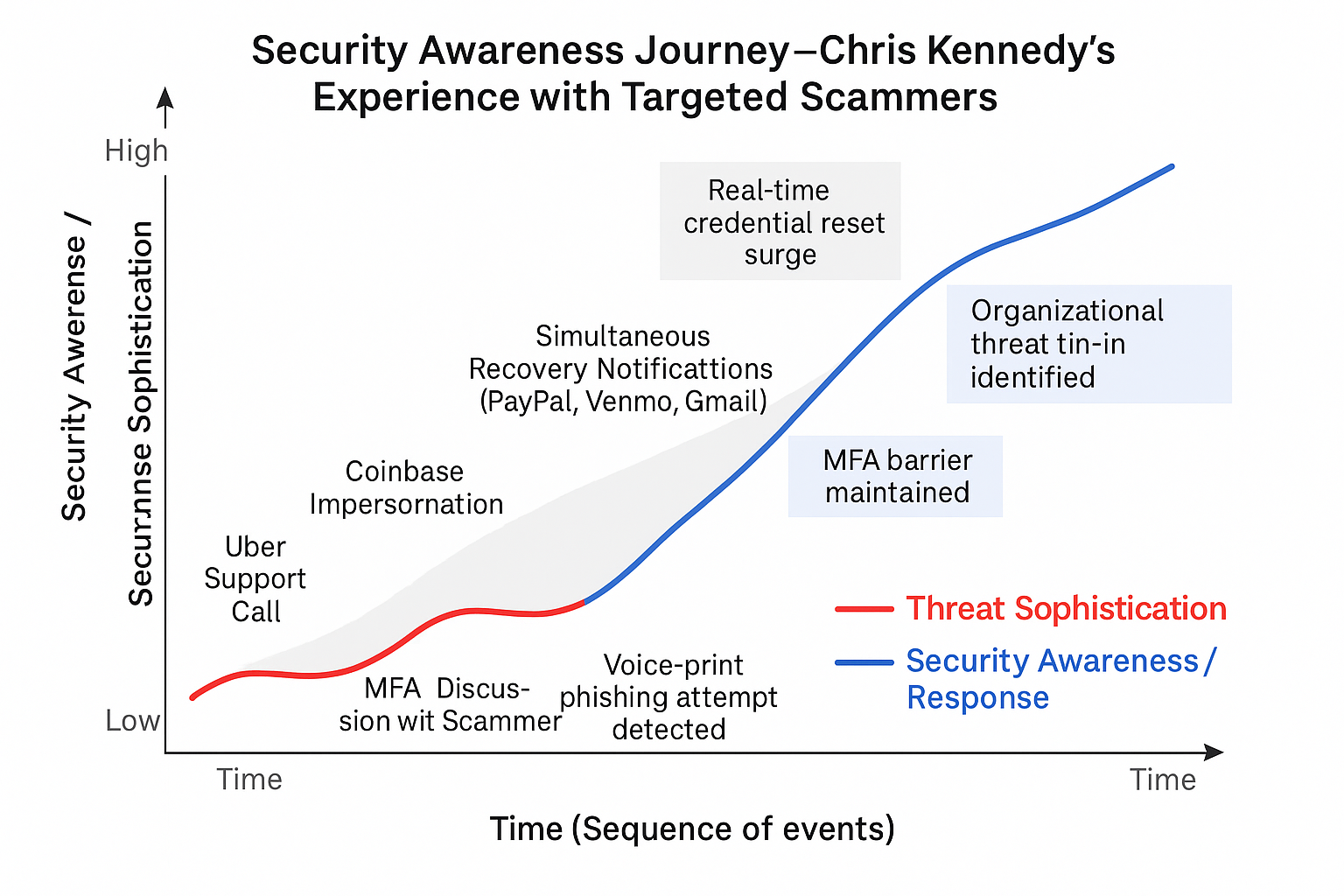
Figure 2: The intersection of Security Awareness and Threat Sophistication
T4: The Coordinated Breach Attempt — Crisis Moment
Timeline: Real-time Attack Threat Sophistication: 🔥 Extreme Security Understanding: 🧠 Critical Awareness
This is where things got serious. Kennedy began receiving simultaneous recovery notifications from multiple services:
- PayPal password reset attempts
- Venmo account recovery requests
- Gmail security alerts
This was a live, coordinated breach orchestration happening in real-time. The attackers were attempting to compromise multiple accounts simultaneously, likely using information gathered from earlier interactions.
Key Takeaway: Real-time fraud orchestration awareness; rapid cold-sweat reaction phase.
Defensive Actions Taken:
- ✅ Did NOT approve any MFA prompts
- ✅ Did NOT click any links in emails/texts
- ✅ Immediately checked accounts directly (not via links)
- ✅ Started documenting the attack timeline
- ✅ Prepared to contact services directly through official channels
T5: Post-Incident Reflection — Connecting the Dots
Timeline: After the Attack Threat Sophistication: 🧩 High (Persistent Threat Landscape) Security Understanding: 🧠 Strategic
After the immediate threat passed, Kennedy took time to reflect on what had happened. He realized that this wasn’t just a personal attack — it demonstrated attack vectors that could affect his organization and anyone else.
Key Takeaway: Understood overlap between personal and enterprise attack vectors.
Strategic Insights:
- Personal account compromises can lead to corporate breaches
- Attackers research their targets extensively
- Security professionals are high-value targets
- The same tactics work on anyone, regardless of technical expertise
T6: Organizational Learning & Advocacy — Turning Experience into Action
Timeline: Ongoing Threat Sophistication: ⚡ Sustained High Security Understanding: 🧠 Leadership
The most valuable outcome of Kennedy’s experience was his decision to share it with the community. By converting this incident into a security awareness campaign, he’s helping others recognize and defend against similar attacks.
Key Takeaway: Promotes multilingual literacy, MFA rigor, and proactive threat sharing.
Organizational Security Culture Elements:
- Share real attack experiences (anonymized as needed)
- Regular security awareness training with real-world examples
- Encourage reporting of suspicious activity without fear
- Foster a culture where security is everyone’s responsibility
- Implement strong MFA policies across all critical systems
The Security Inflection Point
Looking at the graph of this journey, there’s a critical moment where security awareness overtakes threat sophistication. This happened between T4 and T5, when Kennedy’s defensive understanding surpassed the attacker’s advantage.
Visual Analysis
The graph shows two key lines:
🔵 Blue Line: Security Awareness Growth
- Starts at baseline understanding
- Sharp increase during the MFA discussion (T2)
- Peaks during the coordinated attack (T4)
- Maintains elevated state through reflection and advocacy
🔴 Red Line: Threat Sophistication Escalation
- Begins with medium sophistication (realistic impersonation)
- Escalates rapidly during layered attacks (T2-T4)
- Peaks during coordinated breach attempts
- Levels off as defenses hold
⚫ Gray Shaded Zone: Panic / Uncertainty Window (T3-T4)
- The period of maximum stress and uncertainty
- Where many victims make critical mistakes
- Where MFA barriers proved essential
Critical Annotation Callouts
- “Voice-print phishing attempt detected” (T2)
- “Real-time credential reset surge” (T4)
- “MFA barrier maintained” (T4)
- “Organizational threat tie-in identified” (T5)
Lessons for Everyone
1. Trust Your Security Instincts
If something feels wrong, it probably is. Kennedy’s security training kicked in when the MFA discussion didn’t make sense. Even without technical expertise, most people have good instincts about suspicious behavior.
2. MFA is Your Best Friend
Multi-Factor Authentication prevented this attack from succeeding. Even though the attackers had extensive information and used sophisticated social engineering, they couldn’t bypass MFA.
MFA Best Practices:
- Enable MFA on ALL critical accounts (email, financial, social media)
- Use authenticator apps rather than SMS when possible
- Never share MFA codes with anyone
- Don’t approve MFA prompts you didn’t initiate
3. Verify Through Official Channels
When you receive unexpected contact about account issues:
- Don’t use contact information provided by the caller
- Don’t click links in emails or texts
- Look up the official contact information yourself
- Call back or log in directly to check your account
4. Recognize Coordinated Attacks
Modern attackers use multiple personas and channels to create legitimacy:
- “Support” calls followed by “security” emails
- Multiple services apparently affected at once
- Each contact reinforcing the others
Defense: Slow down. Don’t let urgency override critical thinking.
5. Document and Share
Kennedy’s decision to document and share his experience helps the entire community. When you encounter scams or attacks:
- Document what happened (timeline, tactics, claims)
- Report to appropriate services
- Share (appropriately) to help others learn
- Don’t be embarrassed — attackers are professionals
Technical Security Recommendations
For Individuals
-
Enable MFA Everywhere
- Email accounts (Gmail, Outlook, etc.)
- Financial services (banks, PayPal, Venmo, crypto exchanges)
- Social media platforms
- Password managers
-
Use a Password Manager
- Generates strong, unique passwords
- Prevents password reuse
- Helps detect phishing (won’t autofill on fake sites)
-
Stay Informed
- Follow security researchers
- Read security blogs
- Understand current scam trends
- Know what your services’ real security practices are
-
Verify Before Acting
- Independently verify all security alerts
- Never trust caller ID or sender names
- Look for official security indicators
- When in doubt, hang up and call back using official numbers
For Organizations
-
Security Awareness Training
- Use real-world examples like Kennedy’s experience
- Regular training sessions (quarterly minimum)
- Phishing simulations with constructive feedback
- Create a culture of security curiosity, not fear
-
Implement Strong Authentication Policies
- Require MFA for all corporate accounts
- Use hardware keys for high-privilege accounts
- Implement conditional access policies
- Monitor for unusual authentication patterns
-
Incident Response Planning
- Have clear procedures for reporting suspicious activity
- Quick response team for potential breaches
- Communication plans for confirmed incidents
- Regular tabletop exercises
-
Threat Intelligence Sharing
- Share attack patterns with industry peers
- Participate in threat intelligence communities
- Document and analyze attempted attacks
- Update defenses based on emerging threats
The Psychology of Social Engineering
Understanding why these attacks work helps us defend against them:
Exploitation of Trust
Attackers impersonate trusted entities because we’re wired to trust:
- Known brands (Uber, Coinbase, PayPal)
- Authority figures (“security team”)
- Helpful personas (“we’re protecting your account”)
Defense: Verify independently. Trust is earned through secure channels, not claimed over the phone.
Creating Urgency
“Your account will be locked!” “Suspicious activity detected!” “Act now or lose access!”
Defense: Legitimate security issues rarely require instant action. Take time to verify.
Leveraging Fear
Fear of losing money, account access, or having information stolen drives rash decisions.
Defense: Fear is a signal to slow down and think carefully, not to act quickly.
Exploiting Helpfulness
We want to cooperate with people trying to help us.
Defense: Help yourself first by verifying who you’re talking to.
Future Threat Trends
Based on Kennedy’s experience and current trends, expect to see:
1. AI-Enhanced Social Engineering
- Voice cloning for more convincing impersonation
- Real-time adaptation to victim responses
- Automated, personalized attack sequences
Defense: Establish verification methods that AI can’t replicate (family code words, etc.)
2. Deepfake Video Calls
- “Video verification” using deepfake technology
- Convincing executive impersonation for business email compromise
Defense: Use official channels, verify through multiple methods
3. Cryptocurrency-Focused Attacks
- High-value targets due to irreversible transactions
- Sophisticated impersonation of exchange security teams
- SIM swap attacks to bypass SMS-based MFA
Defense: Use hardware wallets, authenticator apps, and exchange-specific security features
4. Supply Chain Social Engineering
- Targeting vendors and service providers
- Using compromised vendor credentials for broader attacks
- Impersonating business partners
Defense: Verify all vendor communications through established channels
Building a Security-Aware Culture
Kennedy’s experience demonstrates the value of security awareness as a cultural practice, not just a compliance checkbox.
Key Cultural Elements
-
Psychological Safety
- People should feel safe reporting suspicious activity
- No punishment for falling for sophisticated scams
- Celebrate catches and near-misses as learning opportunities
-
Continuous Learning
- Regular sharing of new attack techniques
- Real-world examples like Kennedy’s video
- Interactive training, not just boring slideshows
-
Shared Responsibility
- Security isn’t just IT’s job
- Everyone plays a role in organizational defense
- Encourage security curiosity and questions
-
Proactive Communication
- Share threat intelligence promptly
- Warn about trending scams
- Celebrate security wins
Conclusion: The Value of Sharing
Chris Kennedy’s decision to document and share his experience with targeted scammers provides immense value to the security community. By analyzing the attack timeline, understanding the threat sophistication, and recognizing the critical moments where security awareness made the difference, we can all better prepare for similar attacks.
Key Takeaways
-
Even experts get targeted — and that’s okay. What matters is how we respond.
-
MFA is critical — it was the barrier that prevented this sophisticated attack from succeeding.
-
Pattern recognition saves the day — understanding how attacks work helps identify them in progress.
-
Sharing helps everyone — Kennedy’s transparency turns one person’s experience into community learning.
-
Security is a journey — the graph shows awareness growing through experience and reflection.
Final Thoughts
The intersection point on Kennedy’s security awareness journey — where defensive understanding overtook attacker advantage — happened because of:
- Strong foundational security knowledge
- Enabled MFA on critical accounts
- Critical thinking during high-pressure moments
- Willingness to trust security instincts
- Post-incident reflection and learning
We can all strengthen these same capabilities through education, practice, and a culture of security awareness.
Credits & Resources
Full credit to Chris Kennedy for his incredible security awareness video and willingness to share his experience with the community. His transparency helps us all become more security-aware and better prepared for sophisticated social engineering attacks.
Additional Resources
- MFA Setup Guides: Check your service providers’ security settings
- Password Managers: 1Password, Bitwarden, LastPass
- Security News: Krebs on Security, Schneier on Security, The Hacker News
- Training: SANS Security Awareness, KnowBe4
Stay Vigilant
Security is not a destination — it’s an ongoing journey of awareness, adaptation, and learning. Thank you to Chris Kennedy for helping light the way.
Tags: #Security #SocialEngineering #MFA #Phishing #Cybersecurity #IncidentResponse #ChrisKennedy #SecurityAwareness
Share this post to help others recognize and defend against sophisticated social engineering attacks.
Related Posts
Unlocking AI Tentacles: Injecting Context Across Controlled Networks
How the Model Context Protocol turns your private networks into composable context streams that keep AI assistants grounded, auditable, and fast.
Advanced AWS Cloud WAN with Service Insertion — Network Firewall Integration (Part 2 of 2)
Part 2 of 2: Extending your Cloud WAN architecture with AWS Network Firewall service insertion for east-west and north-south traffic inspection using Terraform modules and policy-based routing.
The Audit Agent: Building Trust in Autonomous AI Infrastructure
How an independent audit agent creates separation of powers for AI-driven infrastructure—preventing runaway automation while enabling autonomous operations at scale.
Comments & Discussion
Discussions are powered by GitHub. Sign in with your GitHub account to leave a comment.