Paved Roads: AI-Powered Platform Engineering That Scales Trust
How golden paths, AI copilots, and zero-trust guardrails transform platform engineering from gatekeeper to enabler—shipping accountable GenAI workflows at scale.
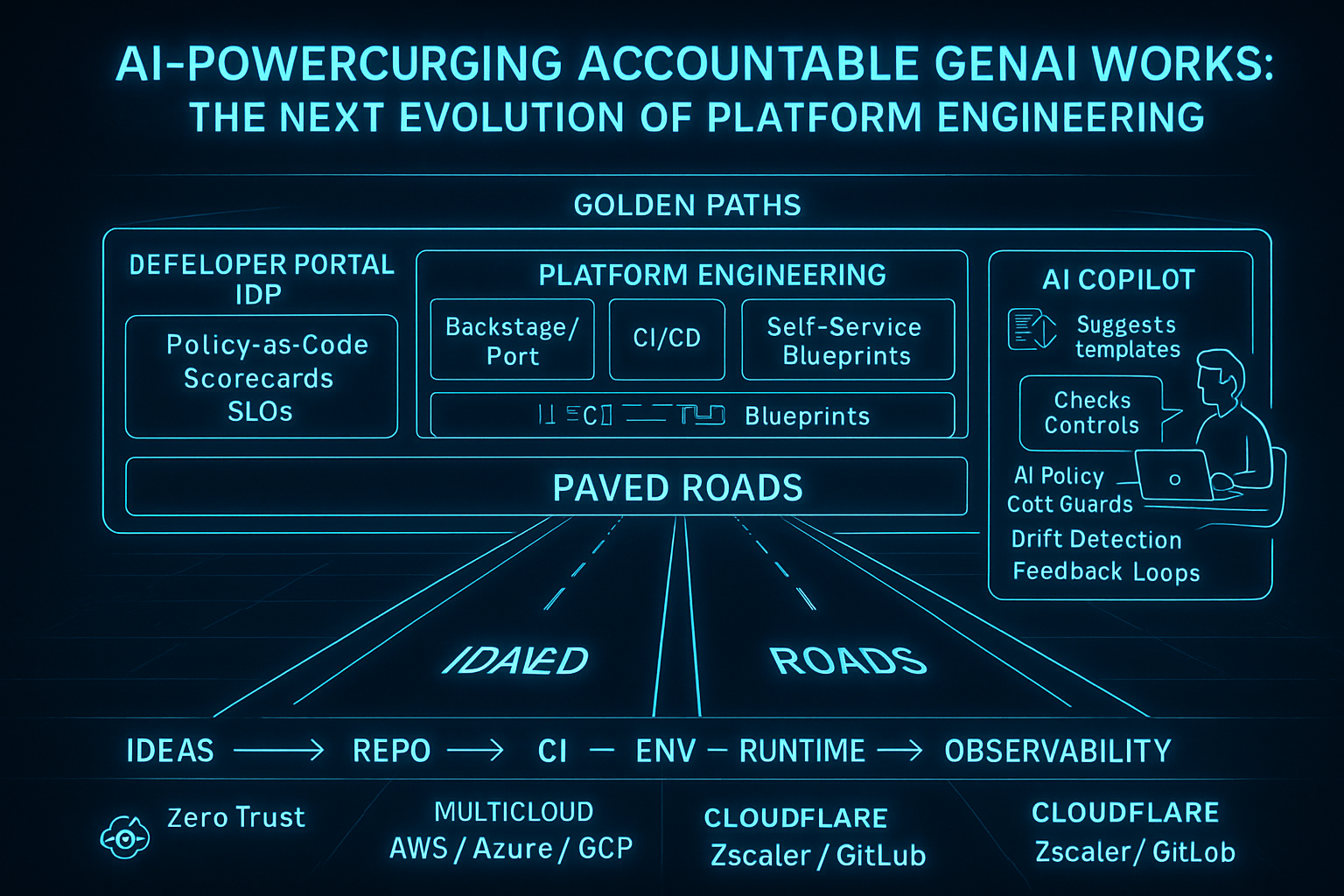
Paved Roads: AI-Powered Platform Engineering That Scales Trust
Platform teams often become bottlenecks: every deployment needs approval, every new service requires custom wiring, and developers wait days for environments. The paved roads philosophy flips that model. Instead of gating every decision, you design golden paths—opinionated, pre-approved workflows that let teams self-serve safely. Layer in AI copilots that suggest templates, check controls, and detect drift, and you get platform engineering that accelerates instead of constrains.
This post walks through the conceptual architecture that powers accountable GenAI works at scale, blending developer portals, platform engineering patterns, and AI-assisted guardrails into a system where teams move fast because the roads are well-lit, not in spite of oversight.
The Golden Paths Framework
graph TB
subgraph Golden Paths
DevPortal[Developer Portal / IDP]
PE[Platform Engineering]
AI[AI Copilot]
end
subgraph Paved Roads
Backstage[Backstage/Port]
CICD[CI/CD]
SelfService[Self-Service Blueprints]
IaC[Infrastructure-as-Code Blueprints]
end
DevPortal --> Backstage
DevPortal --> |Policy-as-Code<br/>Scorecards<br/>SLOs| Backstage
PE --> Backstage
PE --> CICD
PE --> SelfService
PE --> IaC
AI --> |Suggests templates| PE
AI --> |Checks Controls| PE
AI --> |AI Policy<br/>Cott Guards<br/>Drift Detection<br/>Feedback Loops| PE
Paved Roads --> Journey[Ideas → Repo → CI → Env → Runtime → Observability]
Journey --> MultiCloud[Zero Trust<br/>Multicloud: AWS/Azure/GCP]
Journey --> CF1[Cloudflare<br/>Zscaler/GitLab]
Journey --> CF2[Cloudflare<br/>Zscaler/GitLab]Three Pillars
-
Developer Portal (IDP) Your internal developer platform becomes the front door—Backstage, Port, or a custom catalog. Developers see available blueprints, scorecards that show compliance drift, and SLOs that enforce production-readiness. Policy-as-code lives here, not in ticket queues.
-
Platform Engineering This layer owns the paved roads: CI/CD pipelines pre-wired with security scans, self-service blueprints that spin up compliant environments, and IaC templates that embed least-privilege by default. Teams pick a road and drive; the platform ensures they can’t veer into an unmonitored dirt path.
-
AI Copilot The copilot watches over your shoulder—suggesting the right template for a new service, checking that your Terraform includes required tags, detecting when your deployment drifts from policy, and feeding corrections back into scorecards. It’s not approval theater; it’s real-time guidance that keeps teams in the fast lane.
Paved Roads in Practice
From Idea to Observable Runtime
The diagram shows a linear flow that’s anything but bureaucratic:
- Ideas → A developer needs a new microservice
- Repo → They click “Create from blueprint” in the portal, which scaffolds a repo with pre-approved CI config, Dockerfiles, and IaC
- CI → Every commit triggers scans (SAST, license checks, container scans), policy checks (tags, encryption), and automated tests
- Env → Platform code provisions ephemeral dev/staging/prod environments with zero-trust networking, short-lived certs, and observability hooks
- Runtime → The service deploys to a multicloud fabric (AWS, Azure, GCP) fronted by Cloudflare Workers or Zscaler tunnels, with runtime guardrails enforcing least-privilege IAM
- Observability → Logs, metrics, and traces flow into a centralized stack; AI drift detection flags when the deployed config no longer matches the approved blueprint
At every step, the AI copilot is active:
- Suggesting the right compliance template when you deviate
- Auto-generating policy exceptions with context
- Feeding drift signals back into scorecards so platform teams see trends
Golden Paths ≠ Locked Doors
The genius of paved roads is that they’re opt-in defaults, not mandates. If your team needs a bespoke setup—say, a legacy monolith that can’t fit the blueprint—you can still provision it. But the platform tracks that deviation in scorecards, flags it for security review, and nudges you toward migration. You’re not blocked; you’re just visible.
AI-Assisted Guardrails: The Copilot Layer
Traditional platform engineering relies on pre-commit hooks and gating approvals. AI copilots add a third rail: continuous feedback loops that learn from production behavior.
Policy-as-Code + AI Guards
- Cott Guards (context-aware policies): Instead of blanket “no public S3 buckets,” the AI learns that certain buckets (CDN origins, public datasets) are intended to be public. It flags anomalies—new public buckets that don’t match patterns—while letting known-good cases pass.
- Drift Detection: After deployment, the copilot compares runtime state against the IaC blueprint. If someone manually tweaks a security group via console, it raises an alert, suggests a Terraform update, and tracks the drift in your scorecard.
- Feedback Loops: When a policy violation is approved (e.g., “this service needs elevated IAM for legacy reasons”), the copilot records the exception, updates the relevant scorecard rule, and watches for other services claiming the same exemption without review.
Self-Service Blueprints with Embedded Intelligence
The self-service blueprints aren’t static templates. They evolve:
- Template Suggestions: The copilot analyzes your service type (API, data pipeline, static site) and suggests the best-fit blueprint, pre-configured with the right observability, secrets management, and networking.
- Control Checks: As you customize the blueprint, the copilot validates in real-time—“This config lacks encryption at rest,” “Missing required tags for cost allocation,” “IAM role is overprivileged.”
- One-Click Remediation: Instead of cryptic error messages, the copilot offers fixes: “Click here to add AES-256 encryption,” “Auto-apply least-privilege IAM,” “Generate compliant tags from project metadata.”
Multicloud & Zero Trust: The Infrastructure Layer
The bottom tier of the diagram shows the execution fabric: zero-trust multicloud spanning AWS, Azure, GCP, fronted by Cloudflare (Workers, Tunnels, Access) and Zscaler for edge enforcement.
Why Multicloud Paved Roads Matter
If your golden path only supports AWS, you’ve just created a new silo. Multicloud blueprints let teams choose the best runtime for their workload:
- AWS: Lambda + DynamoDB for serverless APIs
- Azure: AKS + Cosmos DB for enterprise SaaS
- GCP: Vertex AI + BigQuery for ML pipelines
The paved road abstracts the differences: the same CI/CD pipeline, the same observability hooks, the same zero-trust networking (via Cloudflare Tunnels or Zscaler Private Access). Developers swap cloud providers by changing a config block, not rewriting the platform.
Zero Trust as Default
Every service gets:
- Short-lived certs from Cloudflare or internal CA
- mTLS between services (enforced by Istio, Linkerd, or Cloudflare’s service mesh)
- Least-privilege IAM generated by the blueprint (AI copilot flags over-scoped roles)
- Network isolation via VPC/VNET segmentation and Cloudflare Access policies
- Runtime attestation so only verified workloads can call APIs
You don’t opt into zero trust; you opt out if you have a documented exception.
Observability: Closing the Loop
The final stage—Observability—isn’t a dashboarding afterthought. It’s the feedback mechanism that makes paved roads self-improving.
Three Observability Modes
- Service Health: Standard metrics (latency, error rate, throughput) flow into Datadog, Grafana, or CloudWatch. SLOs auto-generate from blueprint metadata.
- Policy Compliance: The AI copilot tracks every policy check (encryption enabled? tags present? IAM scoped?), logs violations, and surfaces trends in the developer portal. If 20% of new services skip a required control, the platform team investigates whether the blueprint needs updating or the policy is too strict.
- Drift & Remediation: Runtime drift (manual changes, config skew) triggers alerts and auto-remediation workflows. If someone disables logging on a production bucket, the copilot can either auto-fix (re-enable logging) or escalate to a human with full context (“Bucket
prod-datalogging disabled 3 hours ago, no IaC change”).
Implementation Playbook
Phase 1: Build the Golden Path
- Pick an IDP: Backstage (open-source, CNCF) or Port (commercial, slick UI). Load your existing services into the catalog.
- Define 3 Blueprints: Start small—one for APIs, one for static sites, one for data pipelines. Each blueprint includes:
- Repo template (with CI config, Dockerfile, IaC)
- Required policies (encryption, tagging, IAM)
- Observability hooks (tracing, logging, metrics)
- Wire CI/CD: Integrate your blueprints with GitHub Actions, GitLab CI, or Jenkins. Every blueprint runs the same security checks (SAST, container scan, policy validation).
Phase 2: Layer in AI Copilot
- Policy-as-Code Baseline: Use OPA, Sentinel, or Cloud Custodian to codify your top 10 controls.
- AI Drift Detection: Integrate a tool like Steampipe + Powerpipe (open-source) or Wiz/Lacework (commercial) to continuously compare runtime state against IaC.
- Feedback to Portal: Push policy violations and drift alerts into your IDP’s scorecard. Developers see their compliance score; platform teams see aggregate trends.
Phase 3: Enable Self-Service
- Template Marketplace: Expose blueprints in the portal with search, ratings, and “last updated” badges.
- One-Click Provisioning: Developers fill out a form (service name, cloud, region), click “Create,” and get a fully wired repo + environment in minutes.
- Scorecard Gamification: Show compliance scores on team dashboards. Top-performing teams get recognition; lagging teams get targeted help (not shame).
Phase 4: Multicloud & Zero Trust
- Abstract Cloud Differences: Use Terraform modules or Crossplane to create cloud-agnostic blueprints. Developers specify “serverless API” and the platform picks Lambda (AWS), Functions (Azure), or Cloud Run (GCP).
- Zero Trust by Default: Integrate Cloudflare Tunnels or Zscaler Private Access into every blueprint. No service gets public IPs unless explicitly approved.
- Observability Fabric: Funnel all logs/metrics into a central stack (Datadog, Grafana Cloud, New Relic) so multicloud doesn’t fragment visibility.
Why Paved Roads Win
Traditional platform engineering says “You can’t deploy until we approve your design doc, review your Terraform, and verify your security controls.” That’s a 2-week cycle, minimum.
Paved roads say “Pick a blueprint, customize within guardrails, deploy in 10 minutes. We’ll audit the trail and flag drift, but you own velocity.”
The difference:
- Time to deploy: 10 minutes vs. 2 weeks
- Compliance posture: 100% of deployments follow policy (because the blueprint enforces it) vs. “we think most teams are compliant”
- Developer satisfaction: Self-service with confidence vs. waiting for approvals
And the AI copilot makes it smarter over time: it learns which policies teams struggle with, which blueprints need better docs, and which drift patterns signal real risk vs. noise.
Reference Implementation
The full architecture, Terraform modules, and CI/CD configs live in the aws-global-wan repository. You’ll find:
- Backstage blueprints for multicloud services
- Terraform modules that embed zero-trust networking
- OPA policies with AI-assisted drift detection
- CI/CD templates for GitHub Actions and GitLab
- Observability configs for Grafana + Datadog
Clone it, adapt the blueprints to your stack, and start paving your own roads.
Closing Thoughts
Platform engineering isn’t about control; it’s about leverage. Paved roads give developers safe speed—they can ship daily because the platform guarantees compliance, security, and observability. AI copilots make those roads self-improving—they detect when a policy is too rigid, when a blueprint is missing a common use case, and when drift signals a real problem vs. an edge case.
Ship the golden path. Let the AI watch the edges. And turn your platform team from gatekeeper into enabler.
Want to build your own paved roads? Check out the aws-global-wan repository for production-ready blueprints, policies, and automation.
Related Posts
AI Orchestration for Network Operations: Autonomous Infrastructure at Scale
How a single AI agent orchestrates AWS Global WAN infrastructure with autonomous decision-making, separation-of-powers governance, and 10-100x operational acceleration.
The Audit Agent: Building Trust in Autonomous AI Infrastructure
How an independent audit agent creates separation of powers for AI-driven infrastructure—preventing runaway automation while enabling autonomous operations at scale.
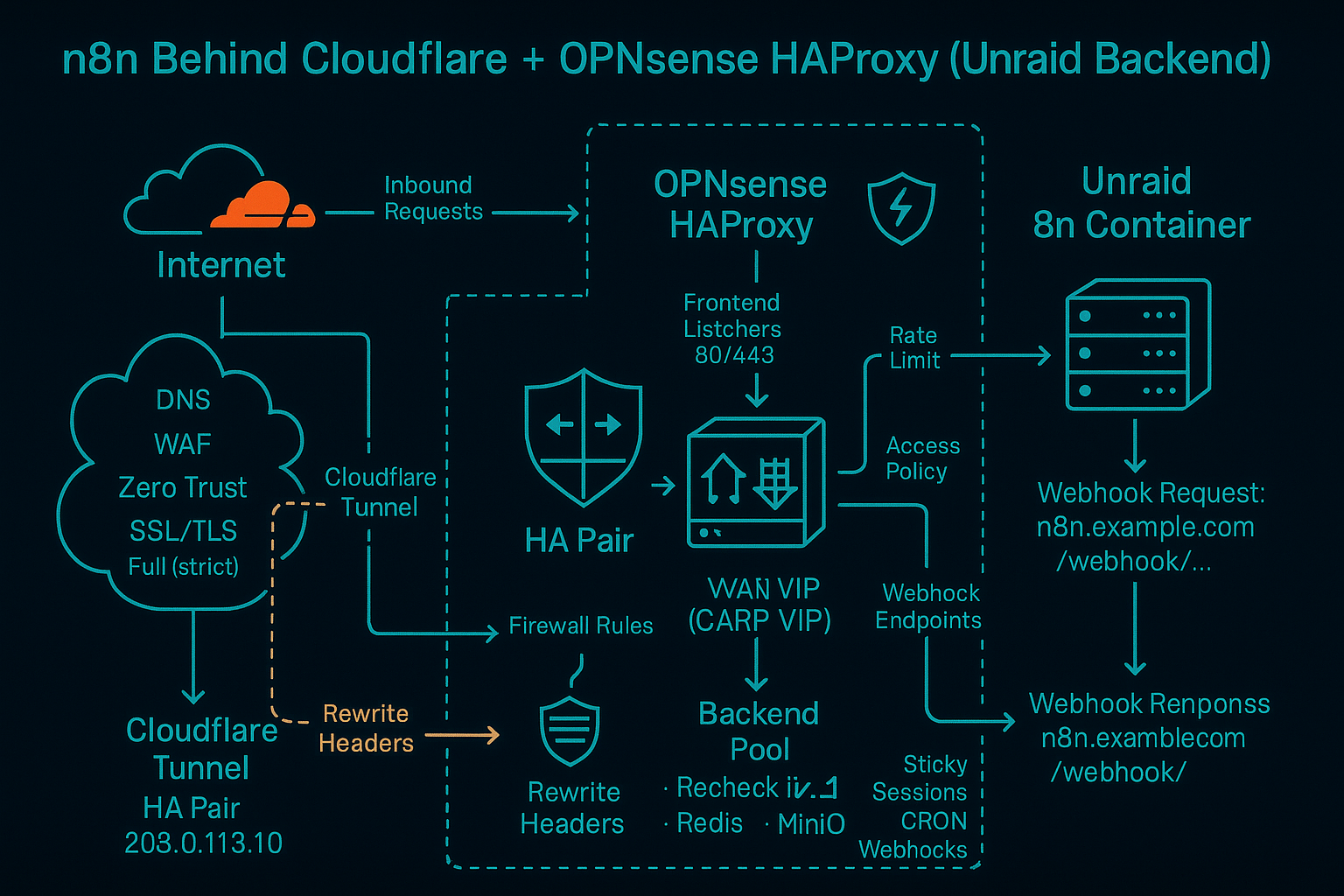
n8n Behind Cloudflare + OPNsense HAProxy (Unraid Backend)
Step-by-step topology for exposing n8n through Cloudflare, OPNsense HAProxy, and Unraid with the right headers, WebSocket support, and TLS expectations.
Comments & Discussion
Discussions are powered by GitHub. Sign in with your GitHub account to leave a comment.